
Anatomy of a secure microcontroller for IoT applications
“Implementing security functions in embedded designs seems to be a difficult task. Microcontrollers (MCUs) that provide security functions have emerged as the times require. They can implement security functions at the beginning of embedded design. This is a good thing, because there is no doubt that a new type of embedded solution is needed to protect Internet of Things (IoT) applications.
“
Implementing security functions in embedded designs seems to be a difficult task. Microcontrollers (MCUs) that provide security functions have emerged as the times require. They can implement security functions at the beginning of embedded design. This is a good thing, because there is no doubt that a new type of embedded solution is needed to protect Internet of Things (IoT) applications.
A study by ABI Research estimates that less than 4% of IoT devices sold last year have embedded security features. At the same time, the market research company predicts that by 2020, nearly 25% of cyber attacks will target IoT devices, making secure MCUs a hot topic.
But what is a secure MCU? Many MCUs claim to provide security features, but after careful study, they are only bragging. This article will discuss in depth the characteristics that define the safety MCU, and introduce the specific features and functions in detail in order to distinguish the safety MCU from the MCU that only claims to have protection functions.
First, MCU vendors seek to supplement their hardware-based security solutions with additional layers of security protection, thereby enhancing their defense against software vulnerabilities and network attacks.
Talking about the cooperation of two MCUs
With the advent of endpoint devices operating at the edge of the network, people need secure over-the-air (OTA) firmware updates. Renesas’ RX651 microcontroller meets this update requirement by integrating Trusted Security IP (TSIP) and Trusted Flash Area Protection, and supports flash firmware updates in the field via secure network communication.
TSIP provides reliable key management, encrypted communication, and tamper detection to ensure strong protection against external threats such as eavesdropping, tampering, and viruses (Figure 1). Similarly, the integrated dual-bank flash memory makes it easier for device manufacturers to perform on-site firmware updates safely and reliably.
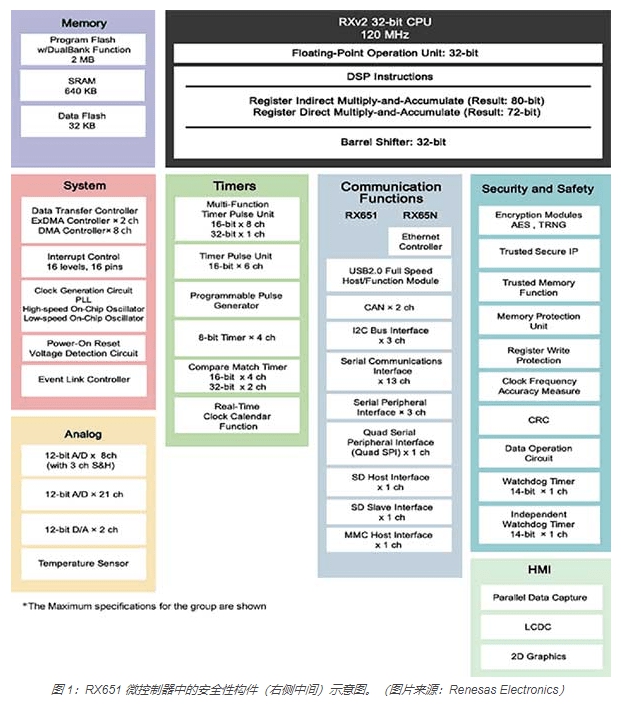
The dual-bank flash memory enables embedded system designers to achieve a high root-of-trust level through the combination of TSIP (used to protect encryption keys) and encryption hardware accelerators (such as AES, 3DES, RSA, SHA, and TRNG). And there is code flash memory area protection to ensure that the boot code is protected from unauthorized reprogramming.
Next, Renesas worked with Secure Thingz, an embedded system security expert, to securely configure its RX series of 32-bit microcontrollers. To this end, Renesas will support the creation of Secure Thingz’s Secure Deploy architecture to simplify the realization of security across the design and manufacturing value chain.
Among the MCU suppliers cooperating with embedded security solution providers, the other is STMicroelectronics. The chip manufacturer is working with Arilou Information Security Technologies to create a multi-layer security configuration in which hardware and software can complement each other to monitor data flow and detect communication anomalies.
STMicro’s SPC58 Chorus series of 32-bit automotive microcontrollers are embedded with a hardware security module (HSM) to protect sensitive security information (such as encryption keys) to ensure that the communication bus in the body and gateway applications is protected from intrusion. HSM provides a hardware-based root of trust to support secure communication, OTA updates, and secure boot.
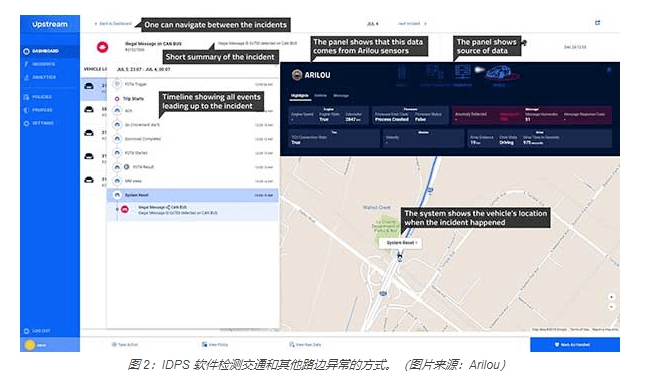
Now, ST has added Arilou’s Intrusion Detection and Prevention System (IDPS) software to the SPC58 Chorus series of automotive MCUs to detect traffic anomalies and form an additional layer of protection against cyber attacks (Figure 2). IDPS is a software solution designed to monitor the controller area network (CAN) bus and detect abnormalities in the communication mode of the Electronic control unit (ECU) in the automotive design.
Dedicated security MCU
The above section briefly introduced MCUs that integrate security functions to deal with physical and remote attacks. This section will describe dedicated safety MCUs, usually called safety components, which are linked via I2C or single-wire interfaces and act as the companion core of the main MCU.
Secure components support MCUs that do not have security functions. They are based on specially constructed hardware to provide a security framework against various threats. These components are simple and cheap, and can reduce the load of security-related tasks (such as key storage, encryption acceleration, etc.) of the main MCU or CPU. This is why they are also called security coprocessors.
In the secure element, all security components work within a common boundary that isolates the authentication key from the software, thereby preventing hackers from attacking, such as power cycling, clock glitches, and side channel attacks. Uploading security keys and certificates to secure components in the factory can also prevent IP theft, design cloning, and product counterfeiting.
Take Microchip’s ATECC608A secure element (Figure 3) as an example. It has a random number generator (RNG) for generating a unique key and meets the latest requirements of the National Institute of Standards and Technology (NIST). The component also has cryptographic accelerators for mutual authentication, such as AES-128, SHA-256 and ECC P-256.
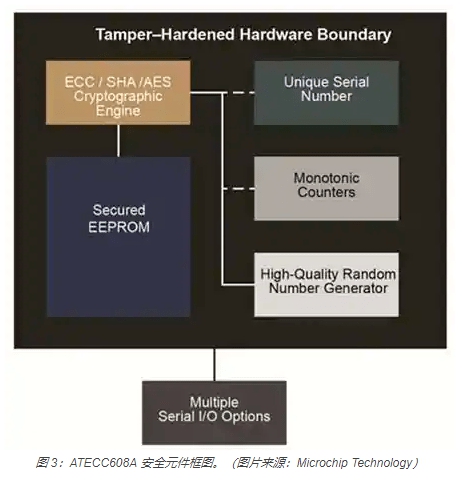
Finally, the secure ROM used for key storage creates an unalterable environment that is difficult to change by hackers and spoofing attacks, thereby preventing tampering and side-channel attacks. All in all, the services provided by ATECC608A range from secure boot to OTA verification, and then to secure key storage and transmission for identity verification of the Internet of Things and cloud services.
Another low-cost MCU dedicated to the realization of security functions is Microchip’s SAM L11 (Figure 4), which can protect power-constrained IoT nodes from threats such as fault injection and side-channel attacks. The device abstracts low-level security details through a modular GUI, allowing developers to select related security functions, thereby simplifying the implementation of embedded security functions.
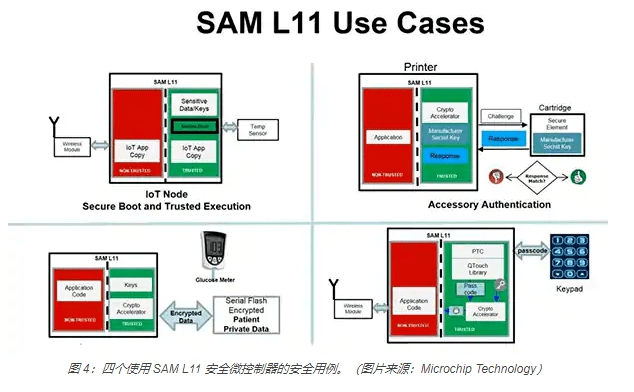
The security functions abstracted by SAM L11 include third-party configuration services. The device also integrates Arm’s TrustZone technology, which isolates secure and non-secure codes in the microcontroller. In addition, SAM L11 simplifies the security requirements of IoT nodes when connecting with cloud services such as Amazon Web Services (AWS).
NXP’s LPC5500 microcontroller is aimed at edge applications of the Internet of Things and is another example of a secure MCU. The device uses the unique key of the device to create an unalterable hardware root of trust. The key can be generated locally by the SRAM-based physical unclonable function (PUF), allowing closed-loop transaction processing between the end user and the OEM. This operation eliminates the need for third-party key processing.
Dedicated security tools
Although security-centric MCUs like ATECC608A include security components to promote a trusted ecosystem, they cannot solve the software isolation problem. Now, the amount of software running on MCUs is continuously increasing, and developers need to protect large code bases from malicious attacks.
For example, IoT devices have protocol stacks for Wi-Fi, Bluetooth, TLS and other functions. Therefore, even if there is no hacker stealing the security key, the damage of the protocol stack will affect the operation of the device. This requires separating mission-critical code from non-mission-critical code and placing critical software in a safe environment.
Arm’s TrustZone environment (Figure 5) separates mission-critical code and protocol stacks from complex operating system (OS) software and large code bases, thereby preventing firmware backdoors from entering the secure key storage area. This environment creates multiple software security domains to restrict access to specific memory, peripherals, and I/O components inside the microcontroller.
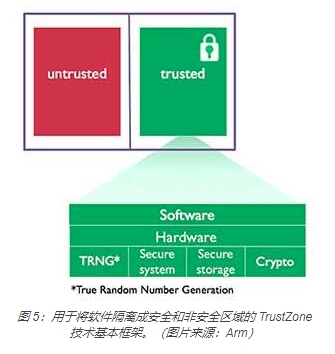
All three types of secure microcontrollers ATECC608A, SAM L11, and LPC5500 (Figure 6) use TrustZone technology, which can isolate secure code from non-secure code. In addition, the ATECC608A secure element can also be used with any microcontroller that supports TrustZone.
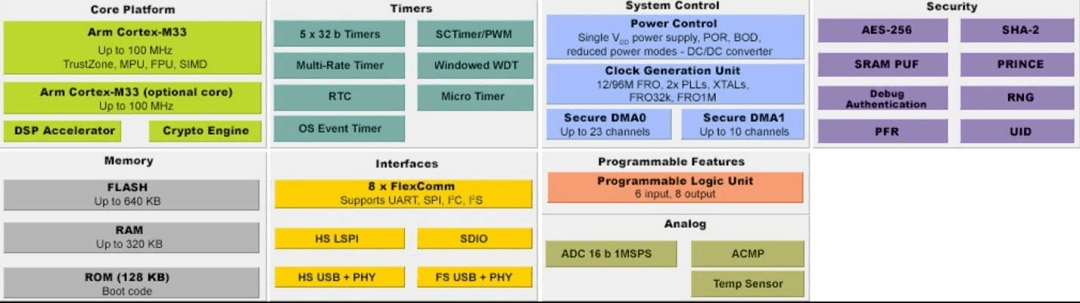
Figure 6: The TrustZone technology in the LPC5500 microcontroller is bundled with the Arm Cortex M-33 processor, as shown in the upper left. (Image source: NXP)
Here, it is also worth mentioning that the security MCU and TrustZone technology are complementary. In a sense, TrustZone requires hardware protection, and security MCUs such as ATECC608A and SAM L11 have contributed to this in the IoT design environment. a little. On the other hand, TrustZone helps build a compact software environment in an MCU-centric embedded design.
Summarize
Through the analysis of safety MCUs, we can understand how they simplify the implementation of embedded safety functions in the design phase and how to bypass the steep learning curve of safety technology expertise. These dedicated MCUs can also reduce cost and power consumption, which are two main considerations for highly constrained IoT designs.
When the rollout of IoT devices exceeds the speed of securely deploying these interconnected designs, a secure MCU can provide a viable way to deal with multiple cyber threats. They provide a simplified solution, equipped with a safe design ecosystem, and promote the formation of a point-and-click development environment.
The Links: FS200R12PT4 1DI200Z-140 TFT-LCD


